Got a frantic phone call this morning, apparently mom was at the police department going on about how her family is poisoning her as she doesn’t want to take her antibiotics and kidney medication. To be clear, not that anyone has been forcing her or otherwise doing anything other than filling her pill organizer with the exacting medication and dosages from the list the hospital provided.
She was in the ICU a few times by now with sepsis due to this exact thing, and it’s not the first time the police have been called out to the house by any means.
The paramedics were apparently at the house last night and verified the correct dosages and medications.
The situation has devolved into such a poor state that anyone who tries to caretake for mom could very well end up on the receiving end of a false police report, which makes it unwise to be in contact with her for fear of their own legal well being.
I’m personally concerned that I may be targeted due to my refusal to move home and mom’s insane rants about how terrible of a person I am for not doing so. It’s not that I don’t want to be there, I want to help mom.
I’m just not sure what else I could possibly communicate on this blog, or otherwise that doing so is not safe. Not for the abuse and name calling she dishes out, for the history of false police reports and insane rants about the government monitoring her, and the flying monkeys of people mom enlists who are financially motivated as she is loud about having money and actively demonizes her husband, children in her life.
There are genuinely good people out there reaching out, trying to help, thank you. It’s an impossible situation and my deepest apologies for not being as controlled and stoic about the situation in the pages of my blog as I could have been. Mike committed suicide, mom had her first melt down at my house and after several hours of insane rambling, the police carried her kicking and screaming out of my front door. Mom becomes very paranoid about people “keeping her in the hospital” and the insane rants and suspicion is shared widely.
If you think this specific situation is insane, it’s been what Mike, Jade and the family have been dealing with semi-privately for months now, and why Mike committed suicide.
It’s been a nightmare.
This is the.. 10th time I believe she’s been in the hospital. I’m questioning to myself, how does it get worse from here, and, how many days until she’s back home again doing the same thing?
Edit: going through previous posts to review, look at what I found from August?

Edit: and yet another one
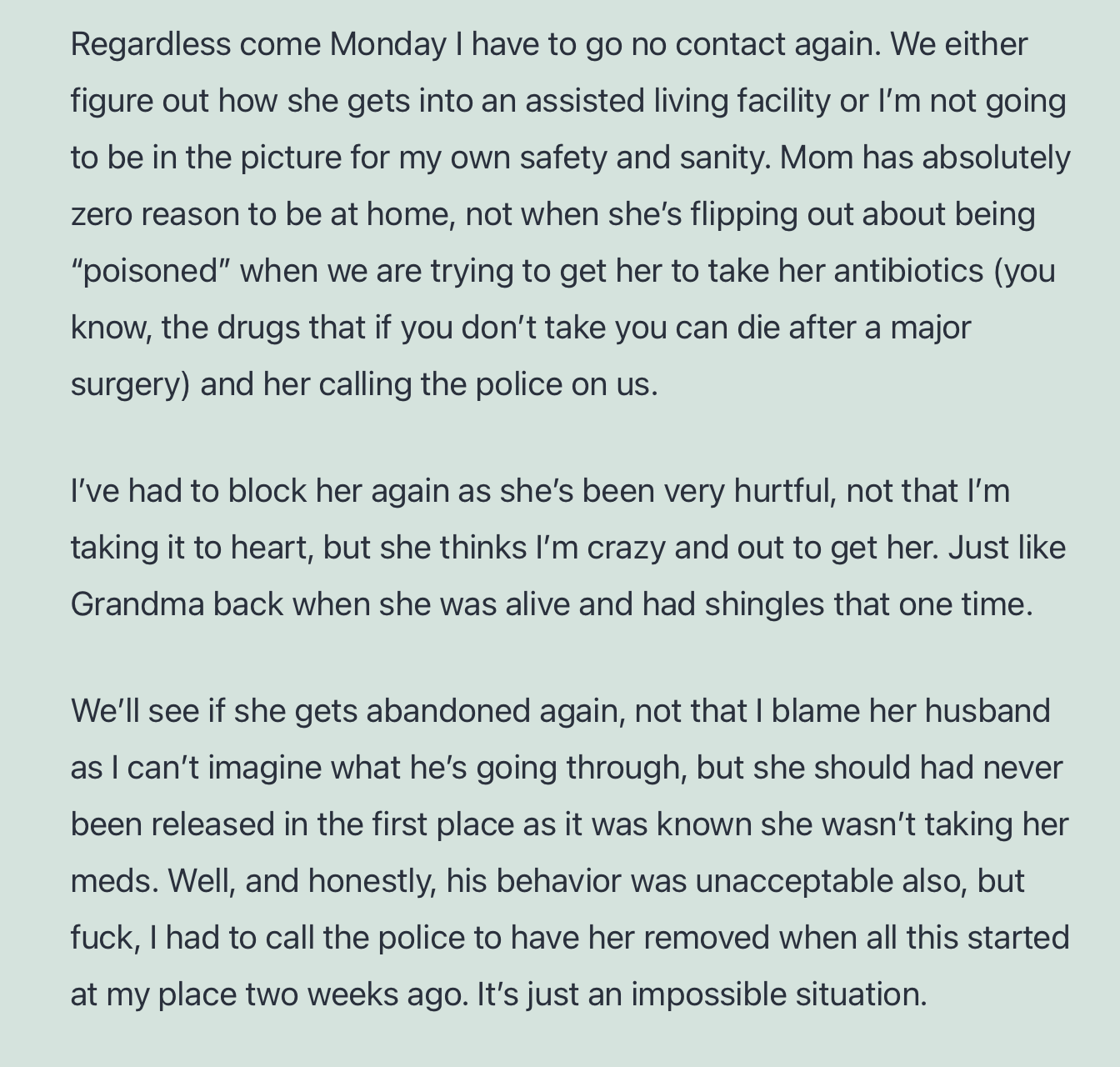
annnddd another from July.
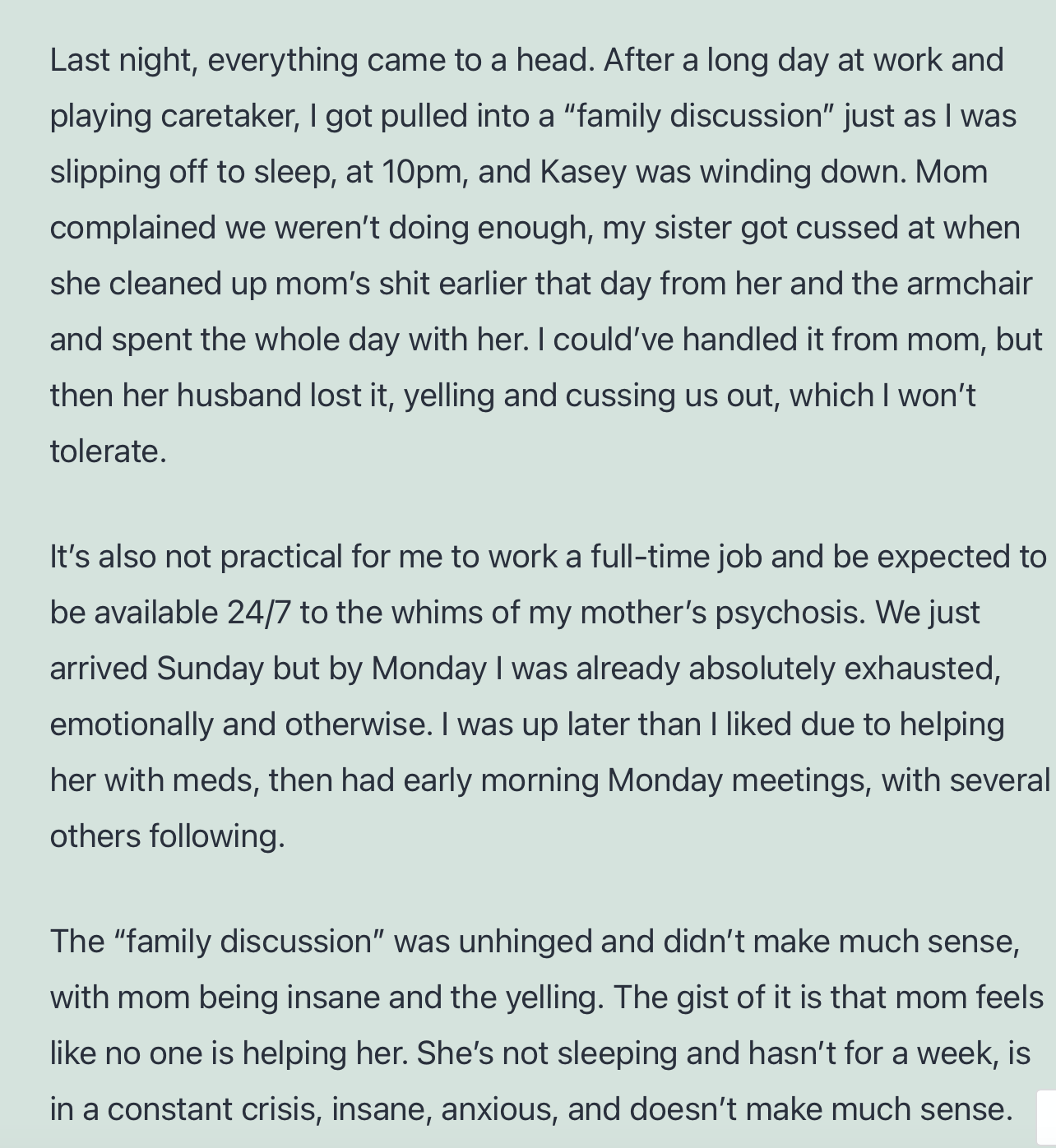
Just to be clear, I later learned that Mike indeed did the best he possibly could and he did try to keep her in the hospital past a certain point, the issue is that the hospital can’t, and it makes sense, even if it’s not ideal.
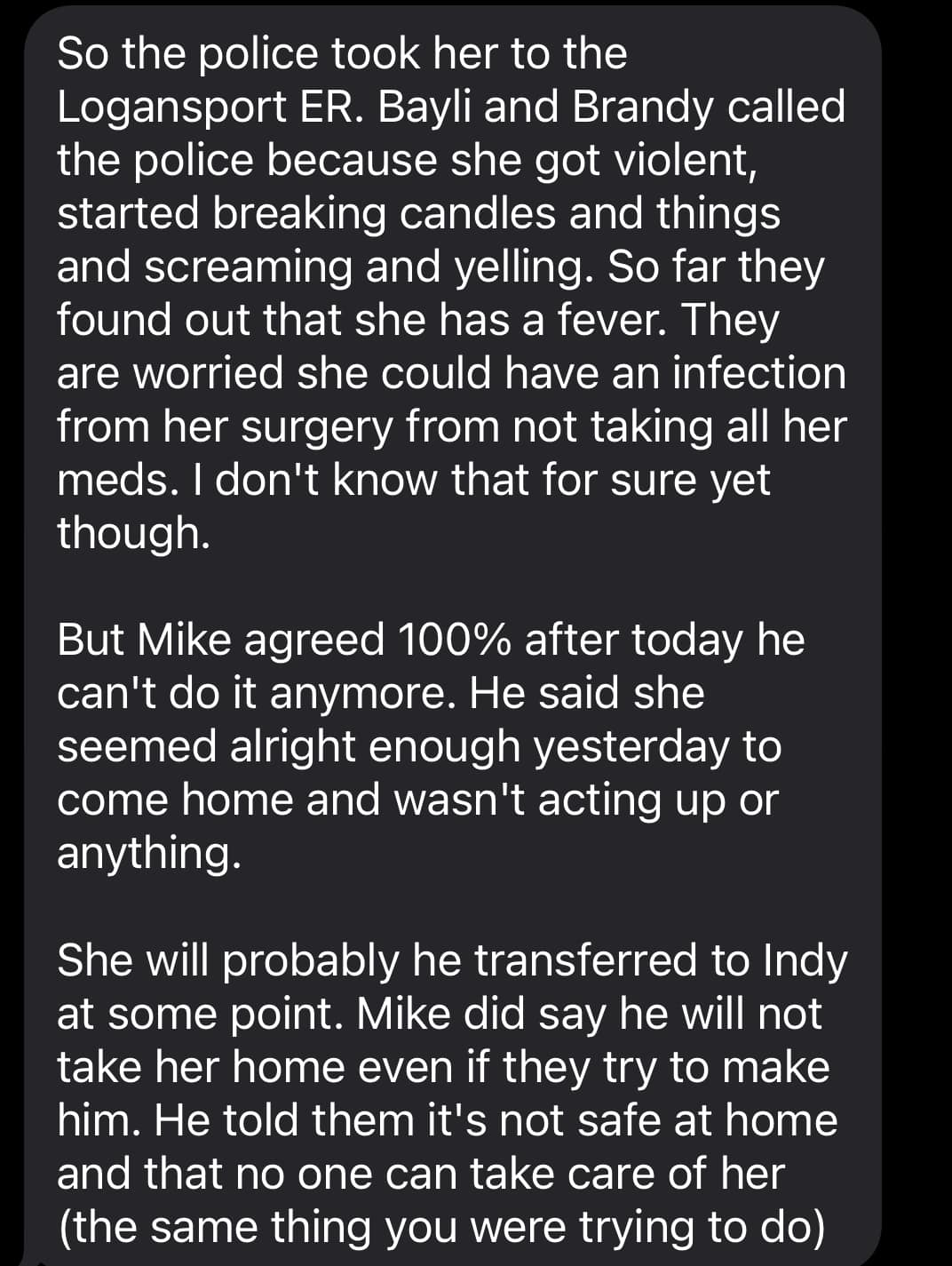
If someone is conscious and able to tell what day it is, the hospital deems them of sound mind, even if they warn the patient and family members they will die if released and return home to do the same things again. The only time a POA or Medical Directive can take effect is that if the patient is on a ventilator or otherwise completely incapacitated.
There is something called emergency guardianship, and I think it’s time to approach that just to ensure that she goes to rehab or a nursing home for a week or two to get stable, instead of in and out of the ICU every week, or like Dr. Mohammad said, she may not make it until Christmas
Edit:
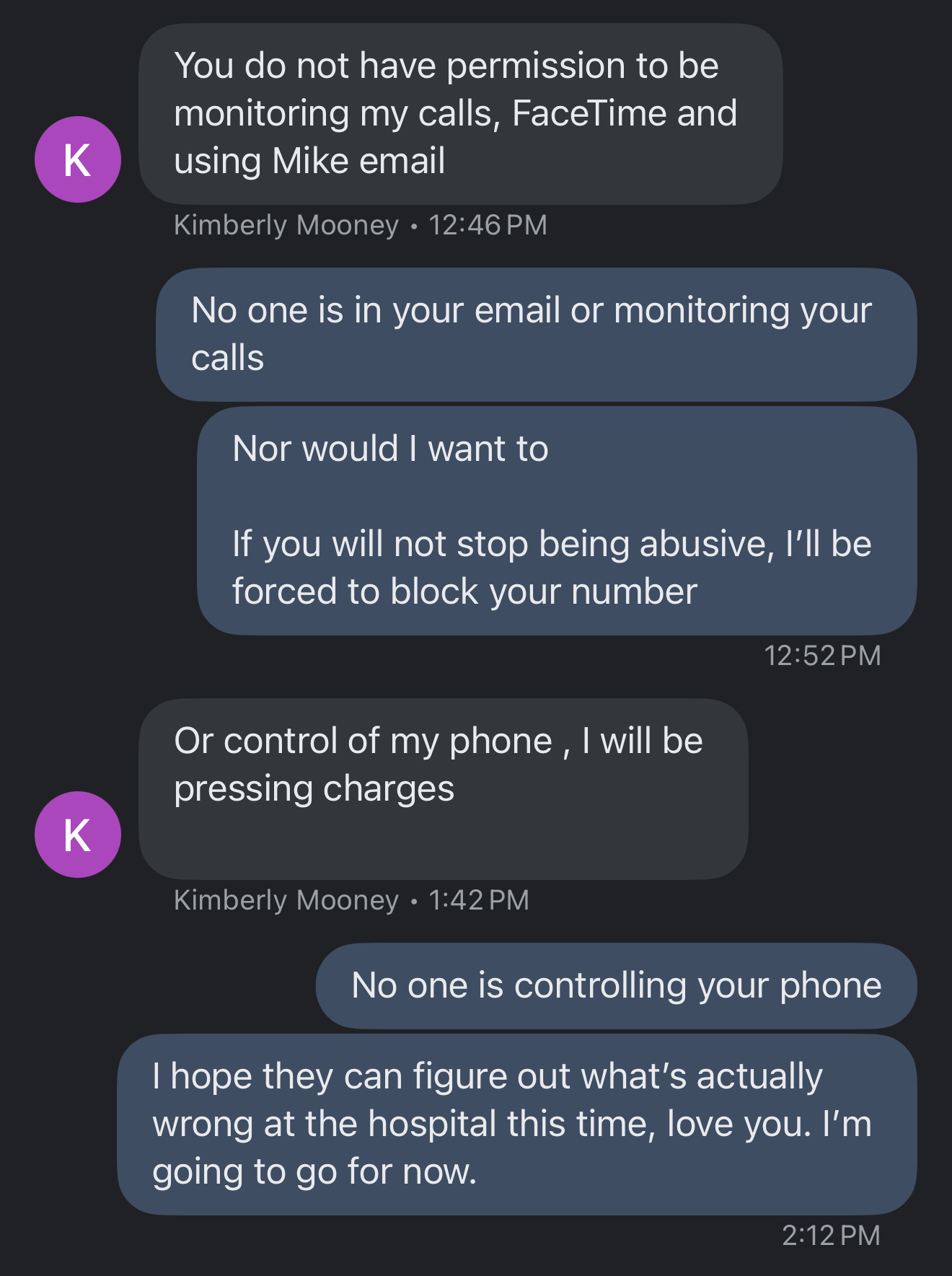
I’ve had to block her.
Leave a Reply